For many organizations, security teams are the first line of defense against all known and unknown threats. The core function of these teams is to identify, investigate and mitigate threats across their entire digital domain. As adversaries become more automated and complex, security teams are relying on a layered approach to prevention.
This approach involves deploying technologies such as Endpoint, Detection and Response (EDR), User and Entity Behavioral Analytics (UEBA) and Network Traffic Analysis (NTA) to gain visibility across their environment. In addition, security teams typically use alert and log aggregation technologies like Security Information Event Management (SIEM) tools to set policies, correlate events and prioritize issues. Finally, there is a need to somehow link the alerts generated with the data to help them investigate and mitigate threats faster.
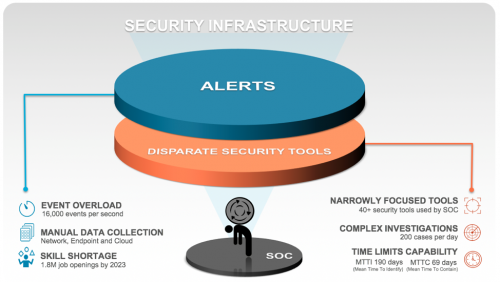
This layered prevention approach comes at the cost of time and expertise. Many security teams are not capable of handling a large amount of alerts. The average SOC might see 174,000 alerts per week. With a finite security team, the math doesn’t work. Security teams may depend on 40+ narrowly focused tools to investigate and mitigate attacks, which can produce 200+ cases per day. This creates a swivel-chair effect that causes security teams to spend time piecing together data and reacting to alerts, rather than being proactive and preventing attacks in the first place.
It takes 197 days to identify a breach within a network, and 69 days to respond to it. No wonder breaches are making headline news. An average cost of a breach in the US was an estimated $7.91M in 2018.

Security teams deserve a better approach that bypasses the complexity and limitations of siloed tools like EDR, UEBA and NTA. An approach that can break the silos and aid the security team at all stages– anomaly detection, alert triage, incident investigation and threat hunting. This ideal approach would:

This is an entirely new approach called XDR, a dramatic departure from the traditional detection and response category. The “X” stands for any data source, be it network, endpoint or cloud, with a focus on force-multiplying the productivity of every member of the security operations team through automation. The ultimate goal is to ensure products within this category reduce mean time to detect and respond to threats without increasing effort somewhere else in the team.
To learn more about this groundbreaking approach, download this whitepaper and get details on how XDR can help you redefine your security operations.
The post Security Teams Deserve a Better Approach to Detection and Response appeared first on Palo Alto Networks Blog.