This piece was originally published August 7 on the Demisto blog.
For the third annual report on the state of SOAR (Security Orchestration, Automation and Response), we at Demisto commissioned a study with 552 security practitioners. Our aim was to find out specific challenges at each stage of the incident response lifecycle, how current product capabilities help overcome these challenges, and what capabilities are missing within security products today.
We define the incident response lifecycle as a continuous and cyclical process that comprises:
- Incident ingestion and enrichment,
- Incident management,
- Investigation,
- Response and enforcement actions, and
- Performance measurement.
For each stage of the lifecycle, we asked respondents:
- What tools they used, and
- What tool capabilities they would place on their ‘wish lists’
The data suggests that security teams are realizing the power of automation. There has been a clear shift among our respondents toward automated and coordinated incident response. Even in areas where there hasn’t been a shift, security professionals have expressed the need for automation and cross-product coordination.
In this blog, we’ll list out our key findings from the report. You can download the entire report below.
Security Teams Want More Automation
A common thread running across the survey responses was an increased willingness to automate and an awareness that automation is needed for efficient incident response today. Below are a few insights from the report:
- Automated playbooks on the rise: More than 50% of respondents use either automated playbooks or a combination of automated and manual playbooks to implement incident response processes. This highlights a clear shift towards automated and standardized response processes that coordinate across security products.
- Security teams desire high-fidelity data: Within the ‘incident ingestion and enrichment’ stage of the lifecycle, 56% of respondents included automated data enrichment as part of their feature wish list. This was closely followed by automated prioritization of alerts (47.8%) and correlation of alerts/indicators across products (47.5%) respectively. Security teams clearly desire more high-fidelity data at their fingertips in order to have more time and information for decision-making.
- Automate to improve: Approximately 61% of respondents wished for ‘machine learning recommendations’ for improving security operations (with only 30% of respondents claiming that this feature was already present in their security products). These ‘measurement multipliers’, when properly executed, will hand more time back to security teams for making decisions that matter.
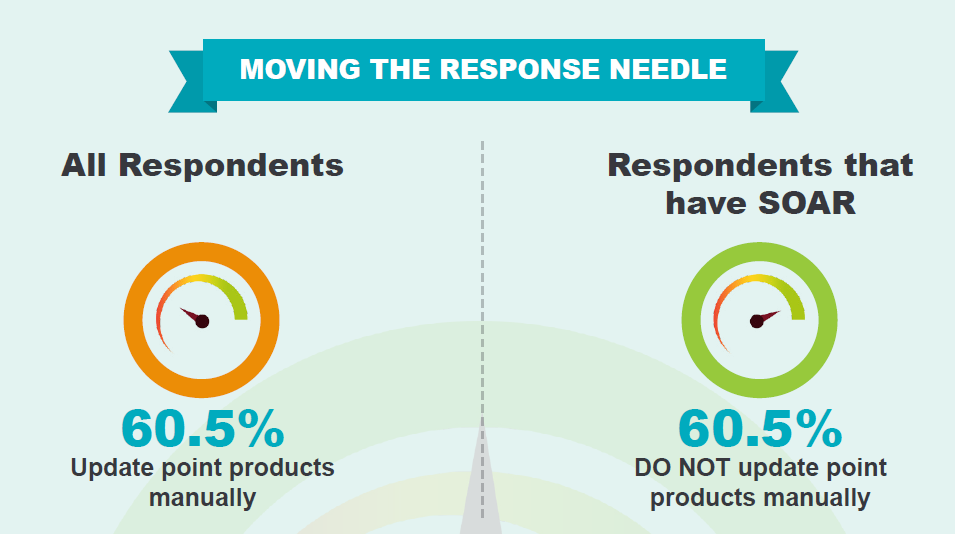
- SOAR makes a difference in response: Around 60% of respondents had to manually perform updates and blocks on different security products. But among respondents that used SOAR, roughly 61% did not have to manually update different point products. SOAR tools have moved the needle towards automated and standardized response.

Hidden Security Challenges
The challenges facing security teams are, perhaps unfortunately, common knowledge by now. A constant rise in alert volume, a stark security skills gap, and disjointed processes have made security operations a tough place to be. In fact, these challenges are so established in the mainstream that the industry has tended to overlook other struggles that are just as troublesome.
Here are a few challenges we uncovered in the report:
- Product silos persist:Approximately 50% of respondents use six or more distinct security tools for incident response. Responding to alerts often means constantly shuffling across different tabs, UIs, and product context, which can result in lost time, increased error rates, and an anxiety-filled work environment.
- Security is a team effort: Security teams must often work with IT teams (85%), NOC teams (53%), and DevOps teams (39%) for incident response. Coordinating across these teams can lead to bottlenecks, process variance, and disjointed documentation.
- Wearing many hats:Security teams can be chameleons on steroids, rapidly changing colors to suit the task at hand. Apart from incident response, they need to oversee vulnerability management (71%), compliance checks (61%), cloud security (41%), and more.
Where Does SOAR Go From Here?
- SOAR tools will be ever-present across the incident response lifecycle: SOAR tools comprised a healthy and growing percentage of common tools used for every lifecycle stage (ranging from 28% to roughly 34%). We predict these burgeoning numbers will rise further as more organizations understand the value that SOAR tools can provide.

- SOAR tools will evolve to provide more standardization and user guidance: Almost 54% of respondents cited the need for industry-specific response templates, and 47% wished that vendors would provide best-practice playbooks. While evaluating SOAR vendors, security teams are bound to gravitate toward tools that have a good balance between out-of-the-box content and the flexibility to create custom content.
- SOAR tools will leverage their general-purpose nature to expand their scope of use cases: We’ve already highlighted how security teams deal with so much more than just incident response. Moreover, around 62% of respondents stated that breach notification laws were affecting their daily operations. Since SOAR tools are comprised of extensible product integrations, drag-and-drop playbooks, and API-driven automation, they can be deployed across these ‘left field’ use cases as effectively as they’re being deployed for incident response today.
Stay tuned for more in-depth blogs that focus on each section of the report. If you’re interested in learning more about SOAR, you can download our eBook – Security Orchestration for Dummies.
The post Security Teams Are Having an Automation Awakening appeared first on Palo Alto Networks Blog.