Introducing Cortex XDR 2.0
Today at our annual Ignite Europe conference, chief product officer Lee Klarich unveiled Cortex XDR 2.0 – the next bold…

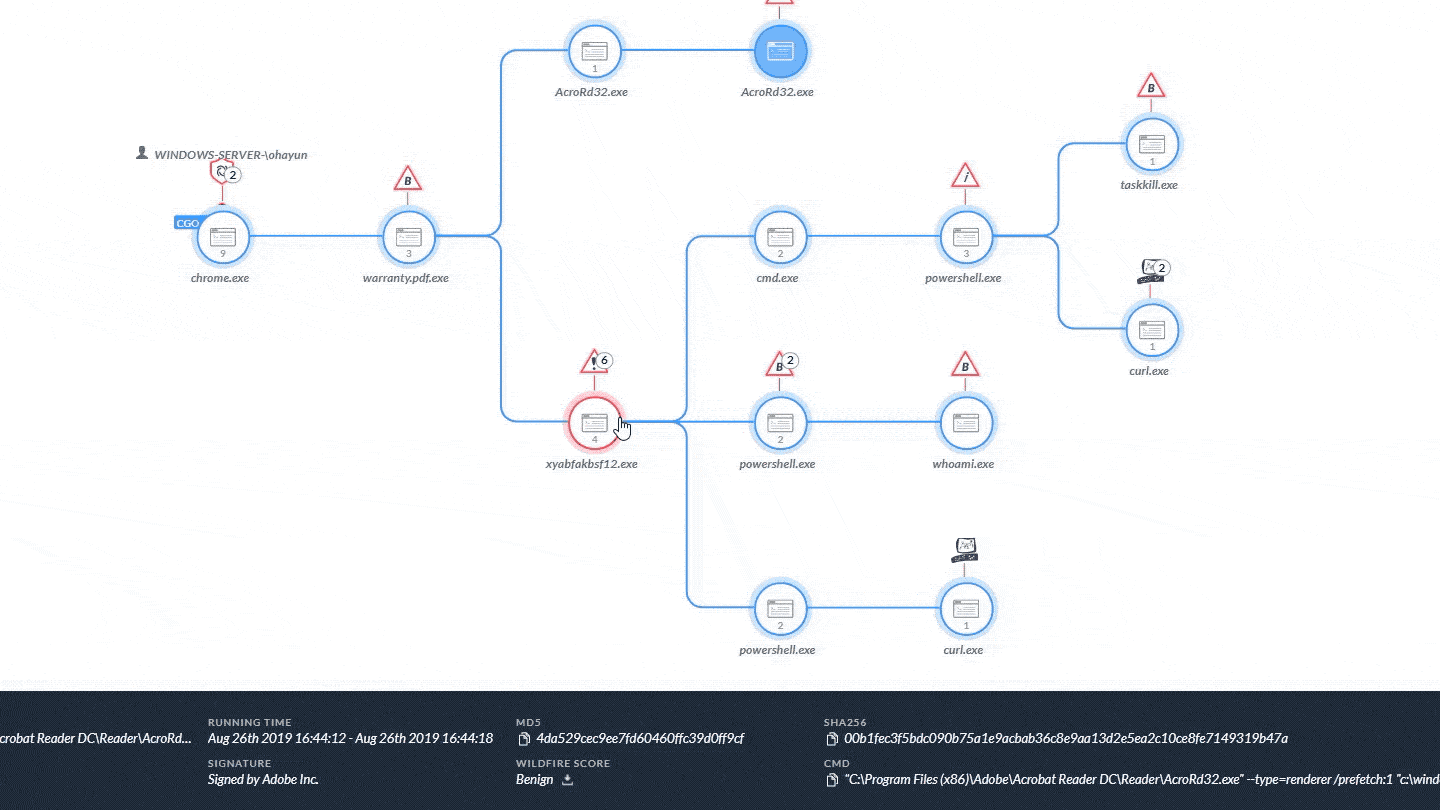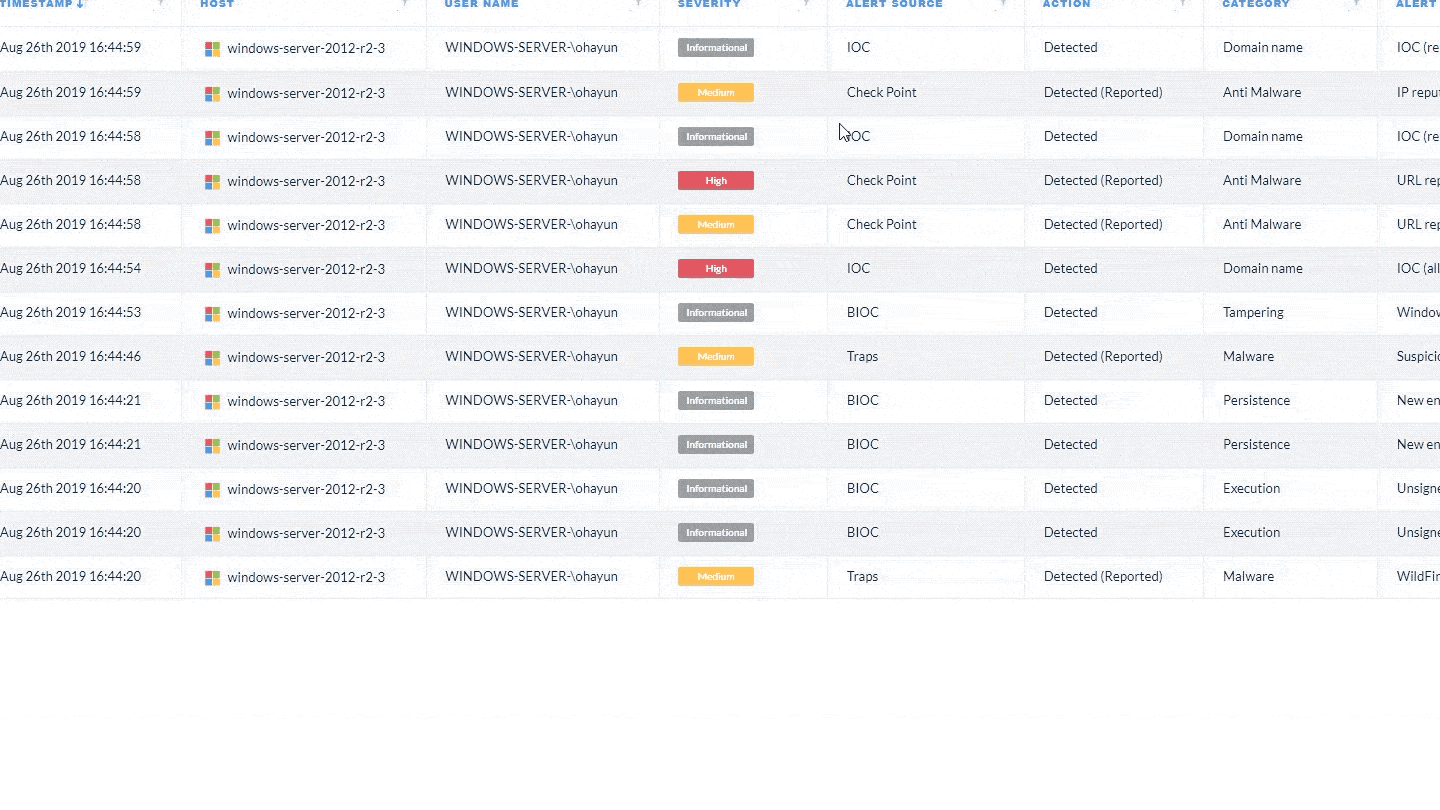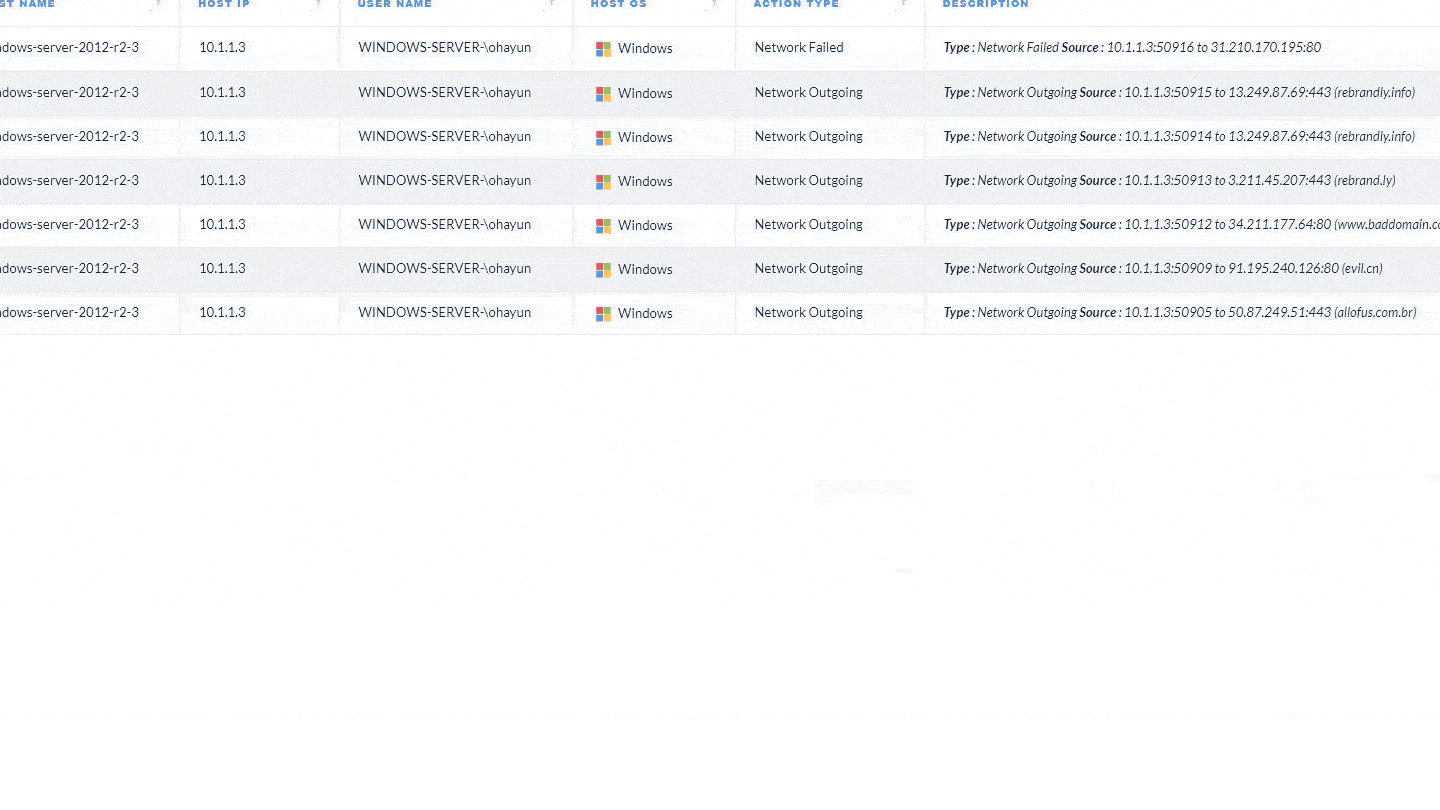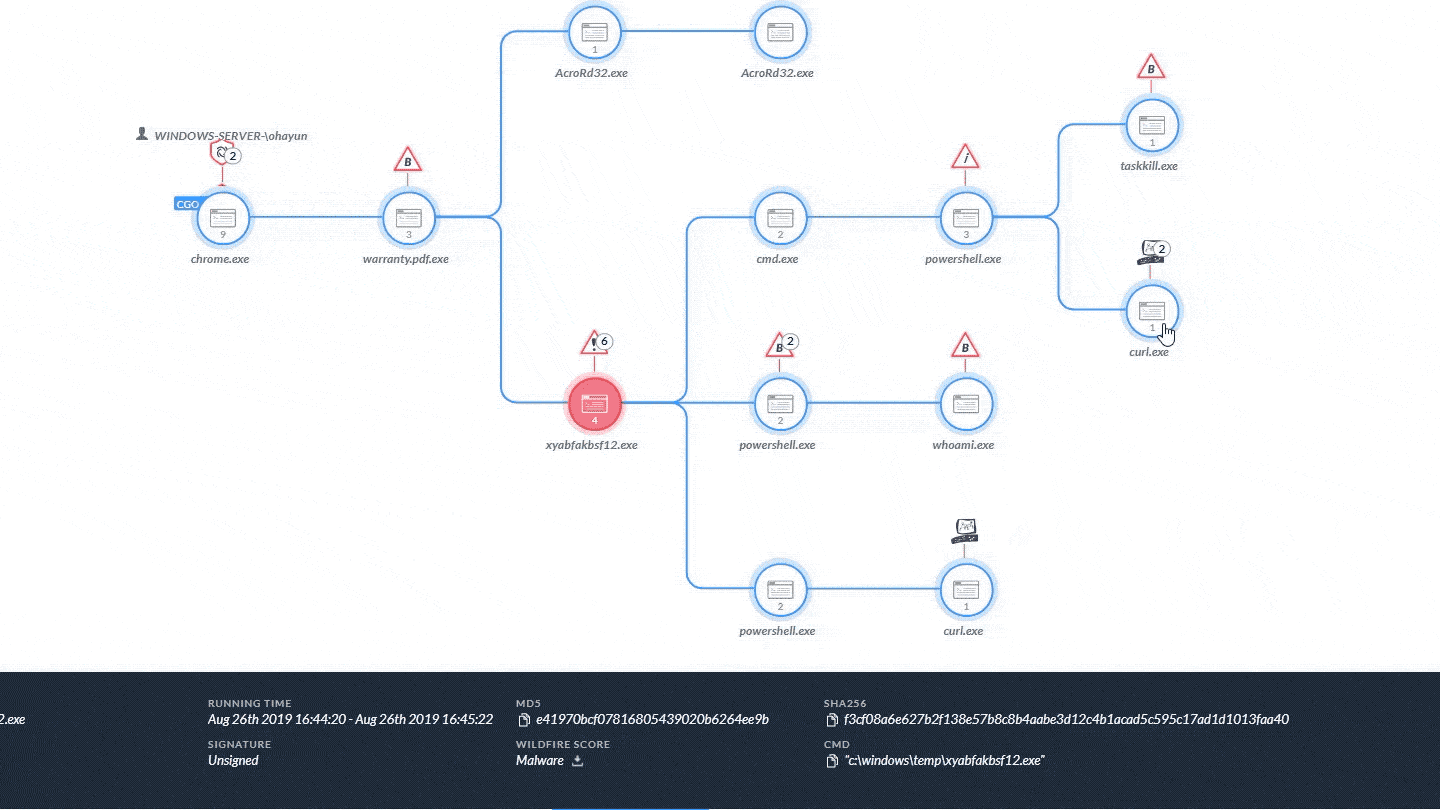
Today at our annual Ignite Europe conference, chief product officer Lee Klarich unveiled Cortex XDR 2.0 – the next bold…
Most enterprises have hybrid or multi-cloud deployments, and maintaining consistent security posture across all deployments is one of their top…
Author: Matthew Chiodi, CSO Public Cloud Applications moving to the cloud and increased user mobility are changing the way networking…
By John Davis, vice president, federal chief security officer, retired U.S. Army major general The cybersecurity industry has a great…
By Ed Metcalf, Director, Product Marketing, Services, Support, Education & Success Tools Palo Alto Networks is known for our technological…
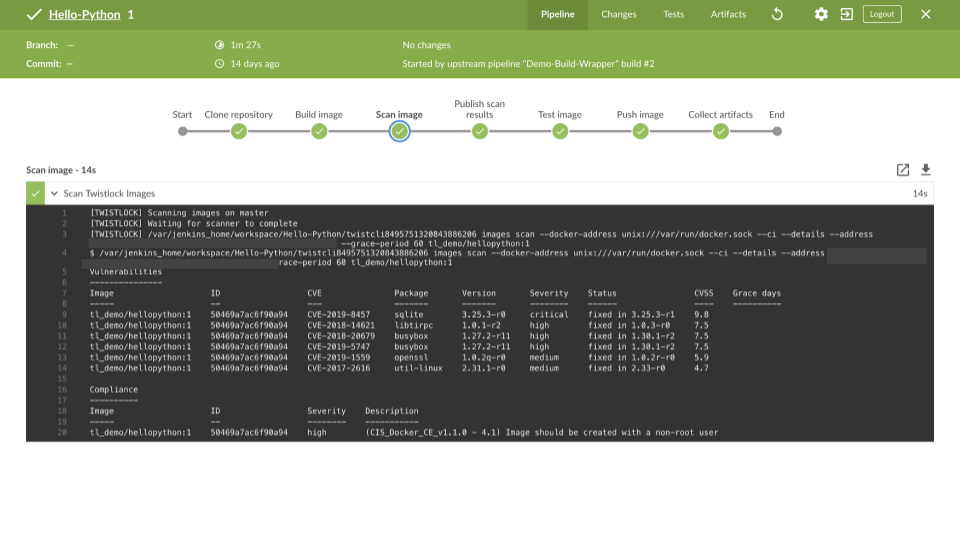
Author: Keith Mokris, Product Marketing Manager, Container Security Today’s enterprises have embraced containers for their simplicity and contribution to improved…
By Nir Zuk, Palo Alto Networks founder and CTO Applications moving to the cloud and increased user mobility are changing the…
Ron Harnik, Senior Product Marketing Manager, Serverless Security One of the most interesting things about working at Palo Alto Networks…
Cyber Canon Book Review: “A Sustainable Digital Economy: Not Fear, but Trust Connects” (2018), by Ad Krikke Book Reviewed By: Fred…
By Christer Swartz, Worldwide Consulting Engineer, Data Center, Virtualization, Service Provider Data centers are changing. The elastic nature of modern application…

Zero Trust, from the beginning, has always had the potential to drive significant impact in the security industry. As a…

By Maryn Eisenhart, president of Palo Alto Networks’ LGBTQIA+ Employee Network I would never have dreamed of how much the…
Cyber Canon Book Review: “A Data-Driven Computer Security Defense: THE Computer Security Defense You Should Be Using,” 2017, by Roger A.…
Palo Alto Networks is a US-based manufacturer that relies on a global supply chain. Some components we import for final…
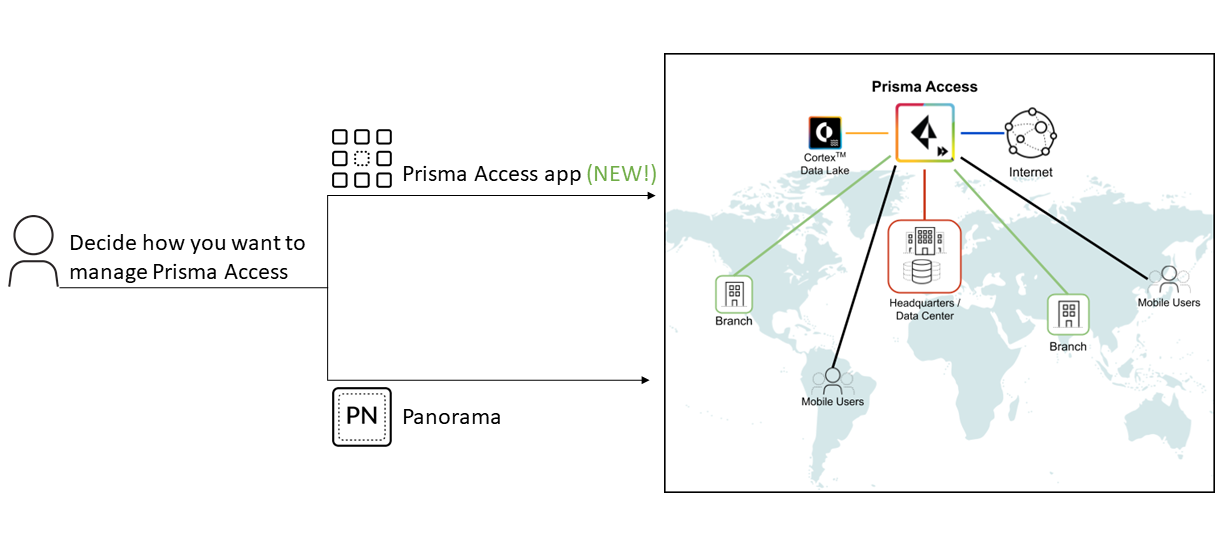
Introducing Cloud Managed Prisma Access! Prisma Access gives you protection at scale, with global coverage for all your users–at headquarters,…
By John Harrison, Regional Product Marketing Manager, EMEA, and Fred Streefland, Regional Chief Security Officer You might be surprised to…
By Evin Safdia, Technical Marketing Manager, Prisma The term “Zero Trust” has been around for almost 10 years, but it…

I am incredibly proud to recognize our Global NextWave Partner Award winners for 2019. This recognition is presented to an…
We modeled the Cybersecurity Canon after the Baseball Hall of Fame and the Rock & Roll Hall of Fame, except for cybersecurity…
Securing headquarters, data centers, branch offices and mobile users isn’t easy – especially when organizations take a traditional approach toward…
I recently visited Dublin, where I met with government and business leaders who are keen on innovating in cybersecurity. It…
We’re excited to launch Beacon – our new digital platform that provides you with a fun, simple way to learn…

This piece was originally published July 31 on Diversity Unscripted. I started my career in pure sciences, specifically in…
On Wednesday, the Kubernetes Product Security Committee disclosed two new vulnerabilities affecting all versions. The issues are related to eight…
From product teams to architects to developers, “shift left” security is becoming more an integral part of everyday vocabulary. It…
In February, we unveiled Cortex XDR, the world’s first detection and response app that breaks down security silos to stop…
Prisma Access (formerly GlobalProtect cloud service) has a new name and introduces new features that you can use for consistent…

Palo Alto Networks is proud that Microsoft has recognized our Unit 42 global threat intelligence team with multiple awards for…
E-commerce is growing steadily worldwide, yet seven out of ten retail purchases are still made in stores. This does not…

This piece was originally published August 6 on Security Roundtable. The people of North Dakota have a lot to be…
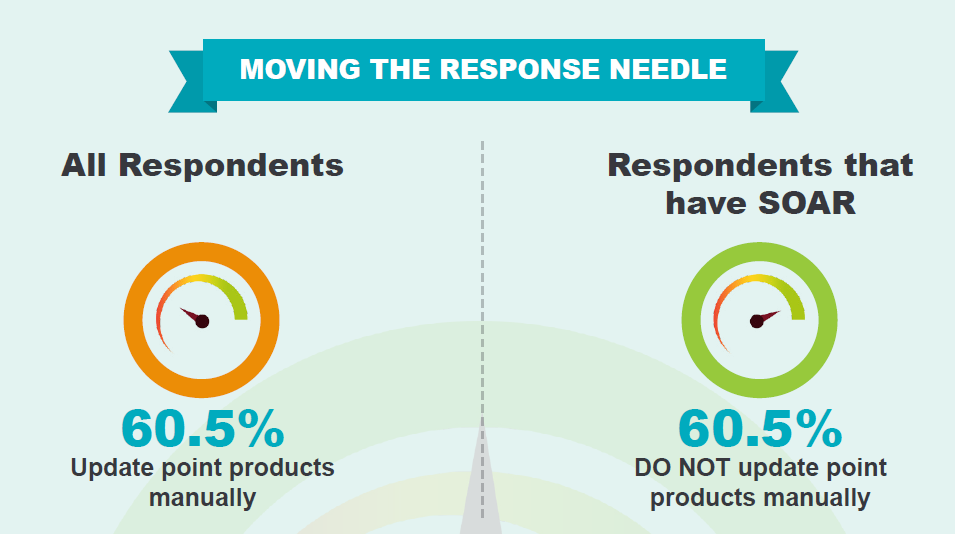
This piece was originally published August 7 on the Demisto blog. For the third annual report on the state of…
Palo Alto Networks founder Nir Zuk last year called for radically transforming the security market by creating a new product…
The Cloud Native Computing Foundation (CNCF) late last year commissioned a penetration test to identify unknown security vulnerabilities and design…
DHI Group runs 100% in AWS. We provide a job recruiting platform for technical candidates and businesses in the United…
Palo Alto Networks achieved a “Recommended” rating in the 2019 NSS Labs Breach Prevention Systems (BPS) test, the highest rating…
For the third year in a row, Palo Alto Networks will collaborate with other top security vendors and experts who…
As a prolific game developer and publisher with six studios across four countries, SEGA Europe needed greater visibility into vulnerabilities…
Traditionally, Change Healthcare operated in a legacy data center environment. That is until about 5 years ago when we set…
Federal agencies face a conundrum: They are the targets of relentless cyberattacks yet lack enough skilled personnel to combat them.…
Last year, three-quarters of the U.S. federal government’s IT budget were spent on supporting and maintaining legacy systems. Combined with…
Lindsey Sanford is the Global Employer Brand Program Manager at Palo Alto Networks. She lives in Reno, Nevada, and has…
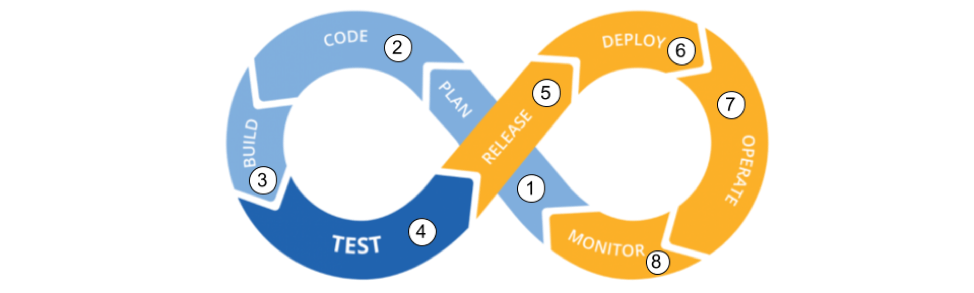
Since the beginning of modern computing, security has largely been divorced from software development. Recent vulnerability research confirms this. Consider…

Palo Alto Networks survey data shows that SOC analysts are only able to handle 14% of alerts generated by security…

Allan Kristensen, Sr. Director, Systems Engineering, Public Cloud at Palo Alto Networks.I recently had the opportunity to chat with Palo…
We are excited to announce that Palo Alto Networks has achieved the highest Security Effectiveness score among all twelve products…
Banking, investment management and FinTech have continually invested in technology upgrades, data analytics and differentiated product offerings in an increasingly…
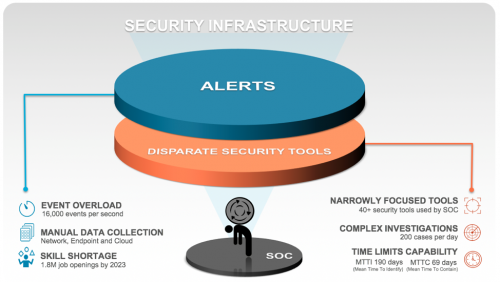
For many organizations, security teams are the first line of defense against all known and unknown threats. The core function…
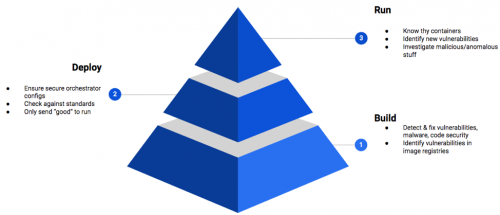
If you’ve been putting off addressing container security, today might be the day to make it a priority. In the…
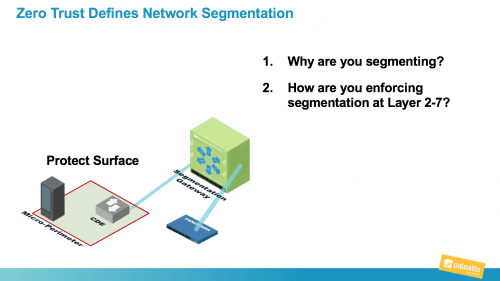
In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology…
Adversaries look for fast and easy ways to steal data. Among the many techniques in their playbooks, using scripts is…

Over the past several months, customers have been asking for the ability to run a Best Practice Assessment (BPA) more…
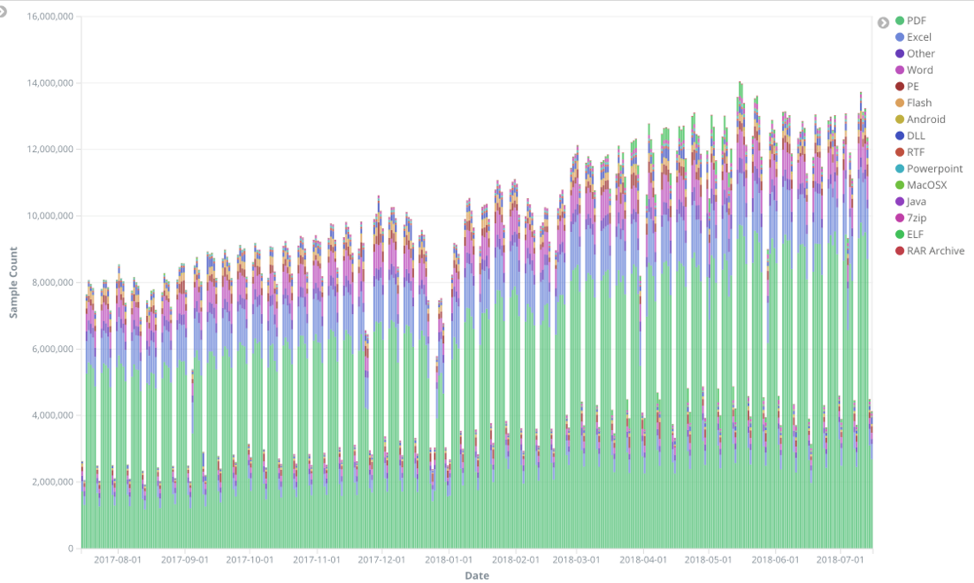
In the never-ending arms race between threat actors and defenders, automation and machine learning have become your ultimate weapons. Today,…

We modeled the Cybersecurity Canon after the Baseball or Rock & Roll Hall-of-Fame, except for cybersecurity books. We have more than 25…

Cybersecurity needs you. Beginning a new career path in cybersecurity can be daunting, especially if you don’t know what to…
Anything that has significant monetary value eventually attracts criminal activity. Such is the case with cryptocurrency, which since its earliest…
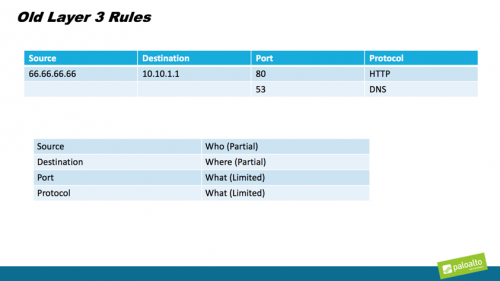
How the Principles of Journalism Help Define Zero Trust Policy Everyone knows that in order for a news article,…
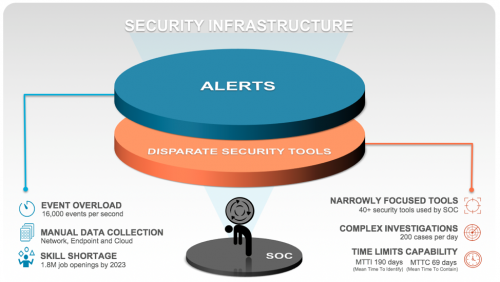
For many organizations, security teams are the first line of defense against all known and unknown threats. The core function…
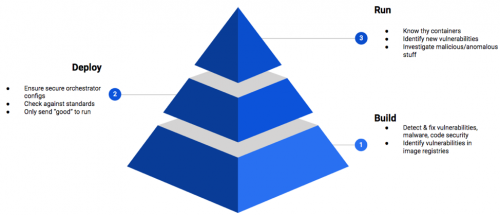
If you’ve been putting off addressing container security, today might be the day to make it a priority. In the…
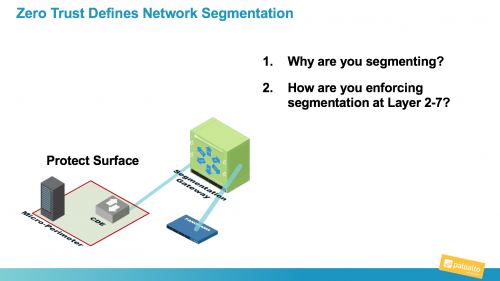
In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology…
Adversaries look for fast and easy ways to steal data. Among the many techniques in their playbooks, using scripts is…

Over the past several months, customers have been asking for the ability to run a Best Practice Assessment (BPA) more…
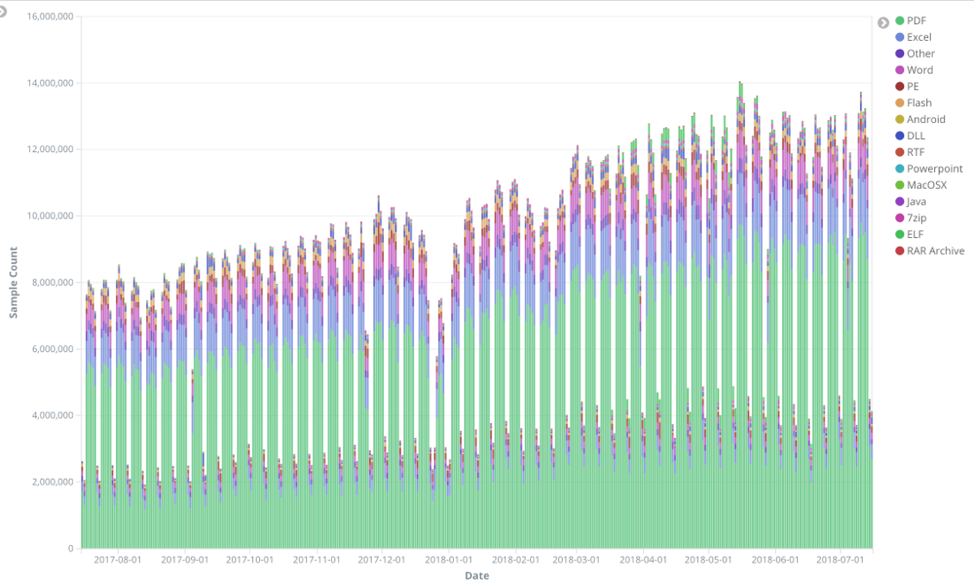
In the never-ending arms race between threat actors and defenders, automation and machine learning have become your ultimate weapons. Today,…

We modeled the Cybersecurity Canon after the Baseball or Rock & Roll Hall-of-Fame, except for cybersecurity books. We have more than 25…

Cybersecurity needs you. Beginning a new career path in cybersecurity can be daunting, especially if you don’t know what to…
Anything that has significant monetary value eventually attracts criminal activity. Such is the case with cryptocurrency, which since its earliest…
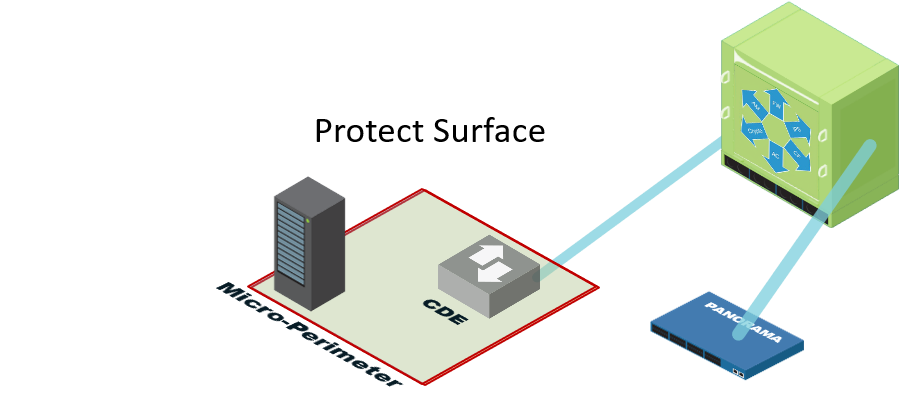
In cybersecurity, one of the things people tend to focus on the least is defining what they’re trying to protect.…